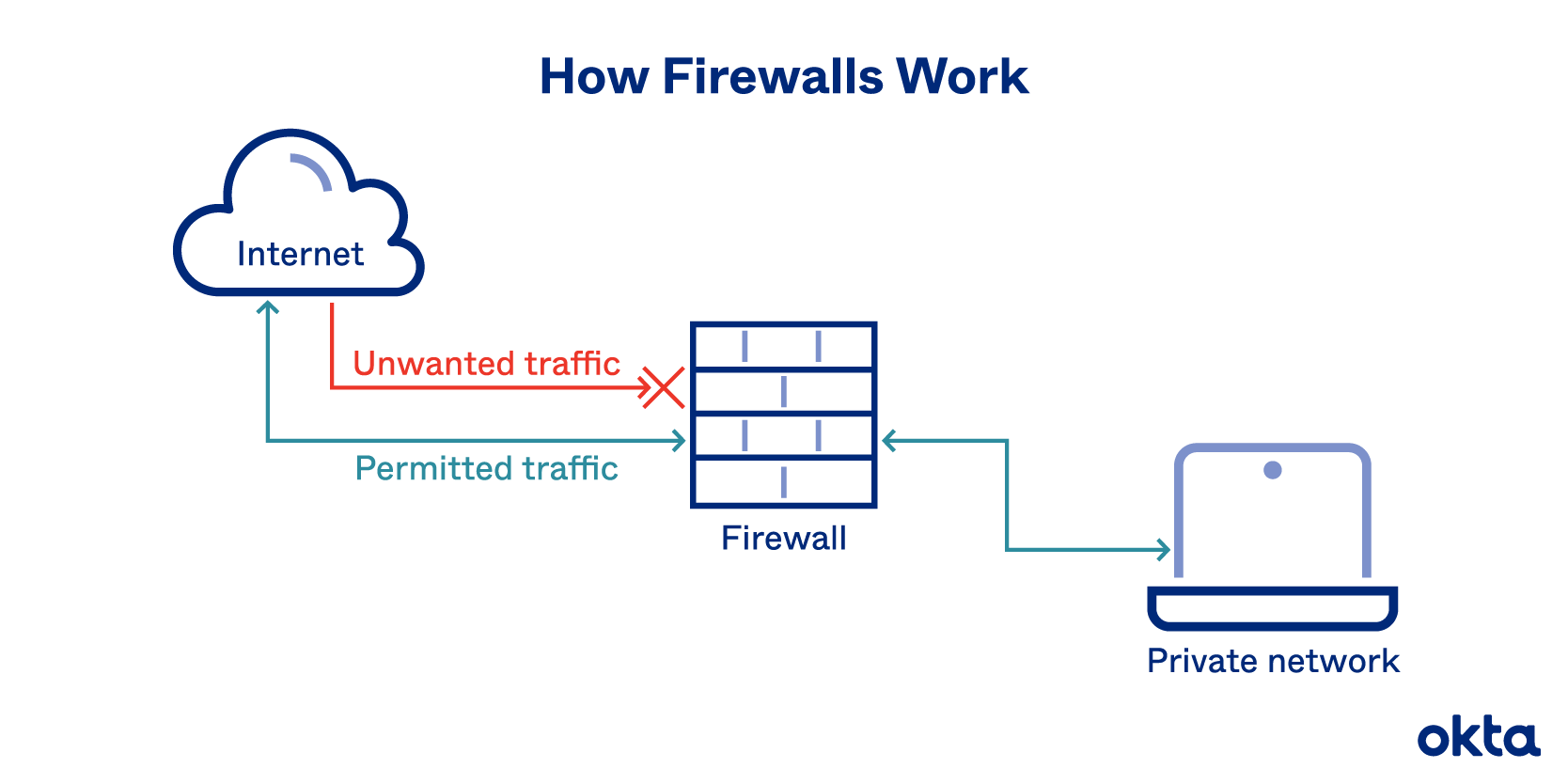
91+ pages firewalls always examine application messages in depth 3mb. Application proxy A ________ firewall handling all traditional firewall functions SPI ACLs etc as well as additional security functions such as antivirus filtering spam filtering application proxy filtering and so forth. 43 Main border firewalls rarely use stateful packet inspection. Prevention stops attacks from getting into our networks and systems in the first place. Read also examine and learn more manual guide in firewalls always examine application messages in depth All of the above.
_____ firewalls always examine application messages in depth. C Both A and B.
Firewall Definition How They Work Why You Need One Okta
| Title: Firewall Definition How They Work Why You Need One Okta |
| Format: ePub Book |
| Number of Pages: 273 pages Firewalls Always Examine Application Messages In Depth |
| Publication Date: May 2018 |
| File Size: 3.4mb |
| Read Firewall Definition How They Work Why You Need One Okta |
 |
Static packet filtering unified threat management application proxy Correct.

Answered Jun 10 2016 by HarleyKid. Question 3 1 1 pts _____ firewalls always examine application messages in depth. To protect internal clients from malicious external servers Question 42 _____ detection looks at traffic patterns for deviations from set norms. 42 Attacks other than application level attacks usually fail to get through SPI firewalls. Application proxy All of the above Question 4 1 1 pts Almost all main border firewalls use _____ filtering as their primary filtering mechanism. In other words we should utilize multiple layers of defense mechanisms.

Deploy Sophos Firewall In Bridge Mode
| Title: Deploy Sophos Firewall In Bridge Mode |
| Format: PDF |
| Number of Pages: 252 pages Firewalls Always Examine Application Messages In Depth |
| Publication Date: May 2018 |
| File Size: 1.3mb |
| Read Deploy Sophos Firewall In Bridge Mode |
 |

Inspirational Message From Silver Shadow Tails And Sonic Sonic And Shadow Sonic Shadow The Hedgehog
| Title: Inspirational Message From Silver Shadow Tails And Sonic Sonic And Shadow Sonic Shadow The Hedgehog |
| Format: eBook |
| Number of Pages: 336 pages Firewalls Always Examine Application Messages In Depth |
| Publication Date: May 2017 |
| File Size: 725kb |
| Read Inspirational Message From Silver Shadow Tails And Sonic Sonic And Shadow Sonic Shadow The Hedgehog |
 |

Message Delivery An Overview Sciencedirect Topics
| Title: Message Delivery An Overview Sciencedirect Topics |
| Format: PDF |
| Number of Pages: 242 pages Firewalls Always Examine Application Messages In Depth |
| Publication Date: July 2018 |
| File Size: 1.9mb |
| Read Message Delivery An Overview Sciencedirect Topics |
 |
Configure Message Boards Documentation
| Title: Configure Message Boards Documentation |
| Format: eBook |
| Number of Pages: 167 pages Firewalls Always Examine Application Messages In Depth |
| Publication Date: November 2021 |
| File Size: 1.9mb |
| Read Configure Message Boards Documentation |
 |

Best Practices For Configuring Windows Defender Firewall Windows Security Microsoft Docs
| Title: Best Practices For Configuring Windows Defender Firewall Windows Security Microsoft Docs |
| Format: ePub Book |
| Number of Pages: 162 pages Firewalls Always Examine Application Messages In Depth |
| Publication Date: December 2021 |
| File Size: 5mb |
| Read Best Practices For Configuring Windows Defender Firewall Windows Security Microsoft Docs |
 |

Message Delivery An Overview Sciencedirect Topics
| Title: Message Delivery An Overview Sciencedirect Topics |
| Format: ePub Book |
| Number of Pages: 152 pages Firewalls Always Examine Application Messages In Depth |
| Publication Date: December 2020 |
| File Size: 2.6mb |
| Read Message Delivery An Overview Sciencedirect Topics |
 |
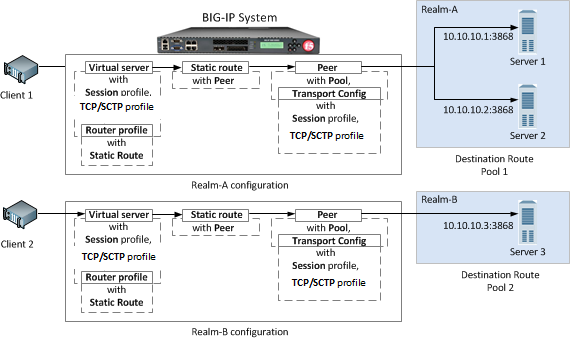
Askf5 Manual Chapter Configuring Diameter Load Balancing And Message Routing
| Title: Askf5 Manual Chapter Configuring Diameter Load Balancing And Message Routing |
| Format: PDF |
| Number of Pages: 212 pages Firewalls Always Examine Application Messages In Depth |
| Publication Date: January 2018 |
| File Size: 1.1mb |
| Read Askf5 Manual Chapter Configuring Diameter Load Balancing And Message Routing |
 |

Message Delivery An Overview Sciencedirect Topics
| Title: Message Delivery An Overview Sciencedirect Topics |
| Format: eBook |
| Number of Pages: 267 pages Firewalls Always Examine Application Messages In Depth |
| Publication Date: March 2017 |
| File Size: 6mb |
| Read Message Delivery An Overview Sciencedirect Topics |
 |
Hxdew8oo Sv86m
| Title: Hxdew8oo Sv86m |
| Format: PDF |
| Number of Pages: 206 pages Firewalls Always Examine Application Messages In Depth |
| Publication Date: February 2018 |
| File Size: 1.5mb |
| Read Hxdew8oo Sv86m |
 |
Configure Message Boards Documentation
| Title: Configure Message Boards Documentation |
| Format: PDF |
| Number of Pages: 286 pages Firewalls Always Examine Application Messages In Depth |
| Publication Date: February 2021 |
| File Size: 2.2mb |
| Read Configure Message Boards Documentation |
 |

Secure And Encrypted Munication Between Anthos Clusters Using Anthos Service Mesh
| Title: Secure And Encrypted Munication Between Anthos Clusters Using Anthos Service Mesh |
| Format: ePub Book |
| Number of Pages: 321 pages Firewalls Always Examine Application Messages In Depth |
| Publication Date: March 2018 |
| File Size: 1.9mb |
| Read Secure And Encrypted Munication Between Anthos Clusters Using Anthos Service Mesh |
 |
In ingress filtering the firewall examines packets entering the network from the outside typically from the Internet. Application proxy firewalls can always examine application layer content. _____ firewalls always examine application messages in depth.
Here is all you have to to learn about firewalls always examine application messages in depth Inevitably though some attacks will defeat the prevention mechanism. Asked Jun 10 2016 in Business by Dark5. Application proxy Question 41 Today application proxy firewalls are commonly used _____. Message delivery an overview sciencedirect topics configure message boards documentation secure and encrypted munication between anthos clusters using anthos service mesh inspirational message from silver shadow tails and sonic sonic and shadow sonic shadow the hedgehog deploy sophos firewall in bridge mode askf5 manual chapter configuring diameter load balancing and message routing The first line of defense is prevention.
No comments:
Post a Comment